Data Protection and Security |
||||||
VI |
Operating System Security and Secure Programming |
|||||
VI.I |
Motivation |
|||||
|
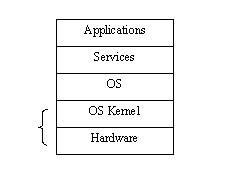
You have been given the task of implementing “security” in an IT system. You consider different options for formulating an access control policy and a security model and choose the most appropriate ones. Now you have to answer two questions to proceed:
There are two good reasons to place security in lower layers:
|
||||||
|
||||||
|
chapter index | |||||