| |
A hash function is a function that takes as input an arbitrary long string of bits and produces a fixed-size result.There are several requirements for a hash function:
- It must be a one-way (pre-image resistance) function: given a message m it is easy to compute h(m) but given a value x it is not possible to find an m such that h(m)=x.
- Second pre-image resistance (weak collision resistance) property: For a given value x, it is computationally infeasible to find x’ such that h(x)=h(x’).
- Collision resistance property: It is computationally infeasible to find two different pairs x,y such that h(x)=h(y).
The first requirement above is crucial for every application using hash functions. Some applications require the additional properties explained above.
As seen from the figure to the right, fast secure hash functions such as MD5 or SHA-1 works as follows:
- The input string X is padded in an unambiguous way to a multiple of the compression function’s block size n.
- Then the padded string X’ is split into m n-blocks X1,...Xm.
- The hash value H(X) = Hm is calculated via the recursion Hi=C (Hi-1, Xi) where H0 is the predefined start value and C is the compression function.
|
|
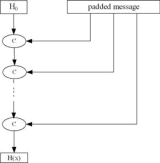
Figure I.I-II
Workflow ow fast secure hash functions. [click to enlarge] |
