Data Protection and Security |
||||||
I |
Secret Key Cryptography |
|||||
I.III |
Message Authentication Codes |
|||||
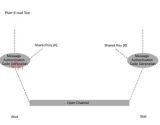
Message authentication code (MAC) is a number that is appended to a message. The purpose is not secrecy but only to authenticate the message using secret-key cryptography e. g. to verify that an email is really coming from your advisor. Assume that you and your advisor share a secret key k. The following simulation (steps) demonstates how to achieve message authentication using a MAC algorithm:
Note that CRC (cyclic redundancy checks) adds redundancy to the message in order to detect unintentional or physical errors in transmission or storage. On the other hand MAC algorithms provide data integrity in spite of intelligent adversaries. We have already seen how message authentication codes can be generated using hash functions. Another standard way is to use a symmetric cipher in CBC mode of operation and send only the last ciphertext block together with the plaintext message. There are also specially-designed MAC algorithms available. |
|
|||||
|
||||||
|
concepts » | |||||