Data Protection and Security |
||||||
VI |
Operating System Security and Secure Programming |
|||||
VI.IV |
Secure Software Development |
|||||
|
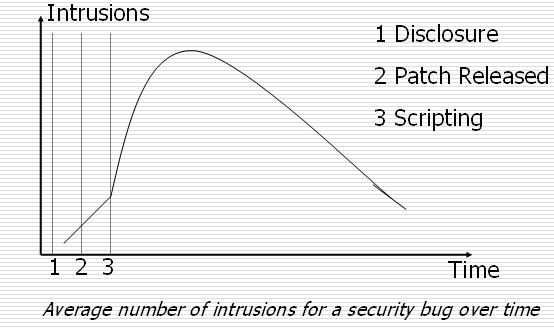
Penetrate and Patch Approach: Penetrate and Patch: Trying to come up with a fix to a problem that is being actively exploited by attackers. This approach has many problems:
The following figure illustrates the windows of vulnerability for a security bug over time as an evidence for the uneffectiveness of patching. Question: What is the alternative?
|
||||||
|
||||||
|
chapter index | |||||