Data Protection and Security |
||||||
VI |
Operating System Security and Secure Programming |
|||||
VI.IV |
Secure Software Development |
|||||
|
Analyzing Security: Security requirements and analysis phase consists of several substeps:
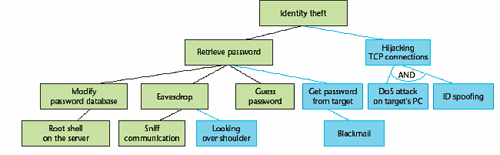
A security environment describes the context in which the software is expected to evolve. The environment affects the kind of threats the application is likely to encounter. For example instant messenger is a client-server application based on exchanging messages over the Internet. High level-security issues lead us to security objectives. Two main security objectives in the instant messenger example are integrity protection of exchanged messages and client authentication. This example is exposed to various threats: identity theft, tampering, eavesdropping. The following attack tree is used to provide a detailed picture of the threat model for identity theft.
The next issue is to write a security policy, a set of security requirements that we can prioritize accordings to the information’s sensitivity.
|
||||||
|
||||||
|
chapter index | |||||