Data Protection and Security |
||||||
VII |
Identification and Entity Authentication |
|||||
VII.II |
Passwords |
|||||
|
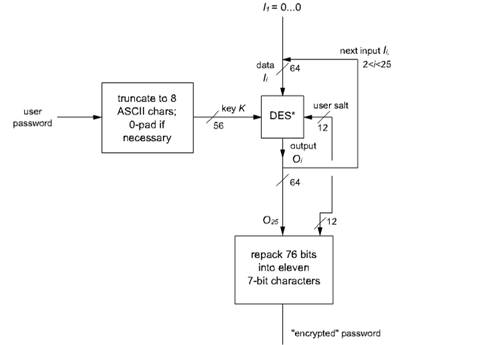
Unix operating system uses conventional password schemes (see Figure 1 and the animation) involving time invariant passwords, which provide so called weak authentication. Like in all fixed password schemes, this system is vulnerable to a number of attacks including replay of fixed passwords, exhaustive password search, password guessing and dictionary attacks. Fixed passwords, if they are sent in cleartext without encryption, are vulnerable to interception while it is in transmit in the network. Another way to capture passwords for the purpose of replaying is installing a keyboard-logger program on the insecure client machine the user uses to enter his/her password. We will say more about this later.
Figure 1. The operation of Unix Passwords A source of good password guesses is a dictionary. Dictionary attacks aim at improving the performance of exhaustive password searches with the help of a dictionary by trying meaningful combinations which is more likely to be chosen as a password. As the computational capabilities of modern computers improve, it is argued that the entropy of a password a typical user can memorize is not adequate even against an exhaustive password search attack. In another view, password guessing attacks can be divided into two groups: online attacks and offline attacks. Online attacks should try each password candidate on the server machine the authentication takes place. To thwart such an online attack, the system can make it impossible to guess too many passwords in this manner. On the other hand, offline attacks are more powerful since the attacker can do the password search entirely without interacting with the server.
|
Animation VII.II-I: The operation of Unix Passwords [ click to enlarge ] |
|||||
VII.II.I Q |
[+] Question
[-] Question
What is the drawback of limiting the number of wrong password entries? |
|||||
VII.II.II Q |
[+] Question
[-] Question
Are the requirements for the online attacks to be conducted? |
|||||
|
||||||
|
chapter index | |||||