Data Protection and Security |
||||||
VI |
Identification and Entity Authentication |
|||||
VII.II |
Passwords |
|||||
|
Password Rules Since dictionary attacks are successful against predictable passwords, some systems impose “password rules” to discourage or prevent users from using weak passwords. These rules include the following:
Insecurity of Passwords: As seen from figure 2, the classical way of authentication via passwords in early protocols is composed of 4 steps:
Consequently, an attacker has four main targets to break the security of a password based authentication scheme:
Maybe the easiest of all four types is the social attack if you can somehow persuade the untrained user to disseminate his password e.g., by introducing yourself as the system admin over the phone. This type of attacks does not only consist of this simple case only but includes
more intelligent and sophisticated techniques. (See the section on phishing attacks.) |
||||||
|
||||||
|
chapter index | |||||
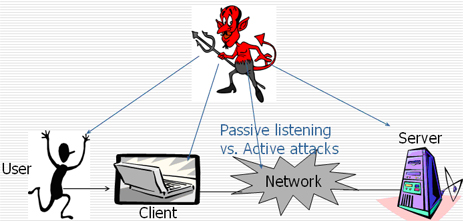 Figure 2. How to Break Passwords
Figure 2. How to Break Passwords