Data Protection and Security |
||||||
I |
Secret Key Cryptography |
|||||
I.I |
Symmetric Encryption |
|||||
Description of DES DES (Data Encryption Standard) encrypts a plaintext bitstring of ‘x’of length 64 using a key K which is a bit string of length 56. The algorithm proceeds in 3 stages:
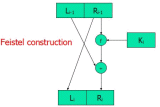
One round of DES encryption (also called as Feistel construction) is illustrated in the figure to the right.The key issue in the operation of DES is the “f function” which is composed of the following stages:
In key schedule, the 56-bit key is used to generate sixteen 48-bit per-round keys, by taking a different 48-bit subset of the 56 bits for each of the keys. S-box is a substitution which produces a 4-bit output for each possible 6-bit input. As you see, the ideas of permutation and substitution we have seen in the last chapter are also widely used in today’s modern ciphers. That is the overview of how encryption works. Decryption works by essentially running DES backwards. Someone, seeing the simplicity of DES, might get the impression that anyone could design an encryption algorithm. However there are critical security choices made in the design process. For instance, if third S-box and seventh S-box are swapped, DES becomes an order of magnitude less secure. |
|
|||||
I.I.Q |
[+] Question
[-] QuestionAre initial and final permutations in the operation of DES really have a security value? |
|||||
|
||||||
|
concepts » | |||||