Data Protection and Security |
||||||
I |
Secret Key Cryptography |
|||||
I.I |
Symmetric Encryption |
|||||
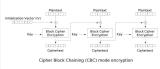
Block Cipher Modes Block ciphers encrypt only fixed-size blocks. If you want to encrypt a plaintext that is shorter than one block size, you can simply pad the plaintext until it reaches the length of full block size. For messages larger than block size, you have to use a block cipher mode. The simplest and unfortunately the least secure mode of operation is Electronic Code Book (ECB) in which you break the message into blocks with block size length and encrypt each block with the secret key. When ECB is used, if a message contains two identical blocks, the corresponding two blocks of ciphertext will be identical. This problem, illustrated in the figures below, might give useful information to the attacker. Another problem with ECB is that an attacker can rearrange blocks or modify blocks to his own advantage. Other modes of operation are proposed to deal with the problems of ECB:
Note that in OFB and CM modes, cryptography can be pre-computed. When the message is ready to be encrypted, the only operation required is XOR. |
|
|||||
I.I.Q |
[+] Question[-] QuestionWhat might be the security problems CBC mode cannot address? |
|||||
|
||||||
|
concepts » | |||||