Data Protection and Security |
||||||
VII |
Identification and Entity Authentication |
|||||
VII.III |
Authentication Protocols |
|||||
|
|
||||||
VII.III.II Q |
[+] Question
[-] Question
What if the clocks Alice and Bob have are not synchronized? |
|||||
VII.III.III Q |
[+] Question
[-] Question
Unlike previous protocol, in its current form this protocol can only be implemented by an encryption algorithm and not by a one-way hash function. Why? Show a modification so that one-way hash functions can also be used. |
|||||
VII.III.IV Q |
[+] Question
[-] Question
There are also public key versions of two protocols we have seen. For instance in Figure 5, you can see a challenge response protocol based on public key signatures. There is another variant based on public key encryption. Can you draw it? 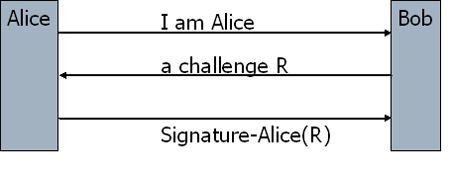 Figure 5. Challenge-Response protocol based on public key signatures. |
|||||
|
||||||
|
chapter index | |||||