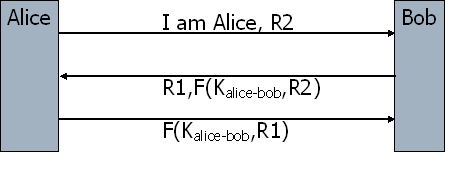Data Protection and Security |
||||||
VII |
Identification and Entity Authentication |
|||||
VII.III |
Authentication Protocols |
|||||
| Mutual Authentication:
In order to do mutual authentication, we can just repeat the authentication procedure in reverse order. Figure 6 shows how we can reduce number of rounds from six to three.
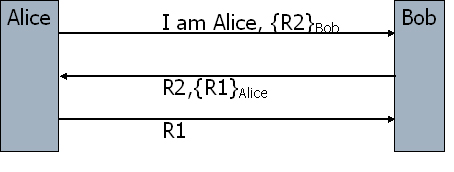
Figure 6. Mutual Authentication based on a shared secret. This variant of the protocol is susceptible to an attack known as reflection attack. The animation demonstrates how this attack works: Suppose the attacker wants to impersonate Alice to Bob. He starts protocol in Figure 6, but can not complete it because he does not know the secret key shared. Now, he opens another session to Bob and uses R1 (Bob’s challenge in the first session) as the challenge. After receiving the response (encrypted R1) in the second session, he is able to send the correct response to Bob’s challenge in the first session without knowing what the shared secret is. To avoid this and similar attacks, there is a general principle which says “don’t have Alice and Bob do exactly the same thing”. There are different solutions derived from this principle. For instance this attack is avoided if Alice and Bob uses different challenges. E.g. odd number for Alice and even number for Bob. Mutual authentication can also be performed with public key cryptography. Figure 8 shows how it can be done with three messages using public key encryption. Note that {R}Alice means R is encrypted with Alice’s public key.
Figure 7. Mutual Authentication based on public key encryption. |
Animation VII.III-I: Reflection attack on Mutual Authentication [ click to enlarge ] |
|||||
|
||||||
|
chapter index | |||||