Data Protection and Security |
||||||
VII |
Identification and Entity Authentication |
|||||
VII.III |
Authentication Protocols |
|||||
|
Mediated Authentication: In previous protocols, we assume that there are a small number of users and each can
If the network is large and each participant wants to authenticate each other, then the manageable solution is based on either
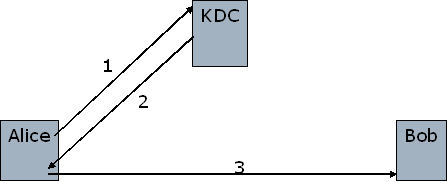
We will see the solution based on CA’s in the next chapter. For now, we only note that using public key cryptography CA’s solve the scalability problem related to requirement of KDC’s to be online. KDC operation involves three steps that can be summarized as follows:
Figure 8. The operation of Key Distribution Center
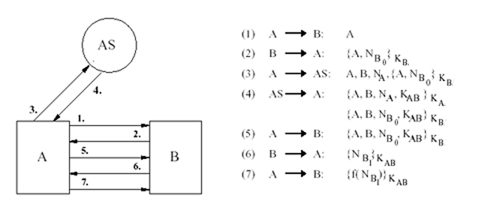
There are numerous KDC-based authentication protocols. One notable example is the Needham-Schreoder protocol illustrated in Figure 10.
Figure 9. The Needham and Schroeder Protocol Note that most symmetric key mediated (KDC based) authentication protocols including Kerberos derive from the seminal work of Needham and Schroeder. We will introduce Kerberos in the next chapter.
|
||||||
|
||||||
|
chapter index | |||||